Have you heard the term “Mimikatz-centric timeline snippet” and wondered what on earth it means? Don’t worry—you’re not alone. This term might sound super technical, but we’ll break it down step by step so it makes sense to everyone, even if you’re not a tech expert. In this guide, we’ll explain what it is, why it matters, and how you can stay safe in a world where cyberattacks keep growing every year.
What Does “Mimikatz-Centric Timeline Snippet” Mean?
To understand this phrase, let’s split it into parts. Mimikatz is a well-known hacking tool. A timeline snippet is like a small piece of recorded activity showing when and how something happened. When you put them together, Mimikatz-centric timeline snippet means a focused view of Mimikatz activity on a timeline—showing when it was used, what it did, and in what sequence during a cyberattack.
This kind of snippet is helpful for cybersecurity teams. It lets them analyze attacks, understand how hackers moved through a system, and respond faster to threats. In short, it’s a tiny but powerful piece of a larger cyber incident timeline.
Breaking Down the Name – Mimikatz Explained
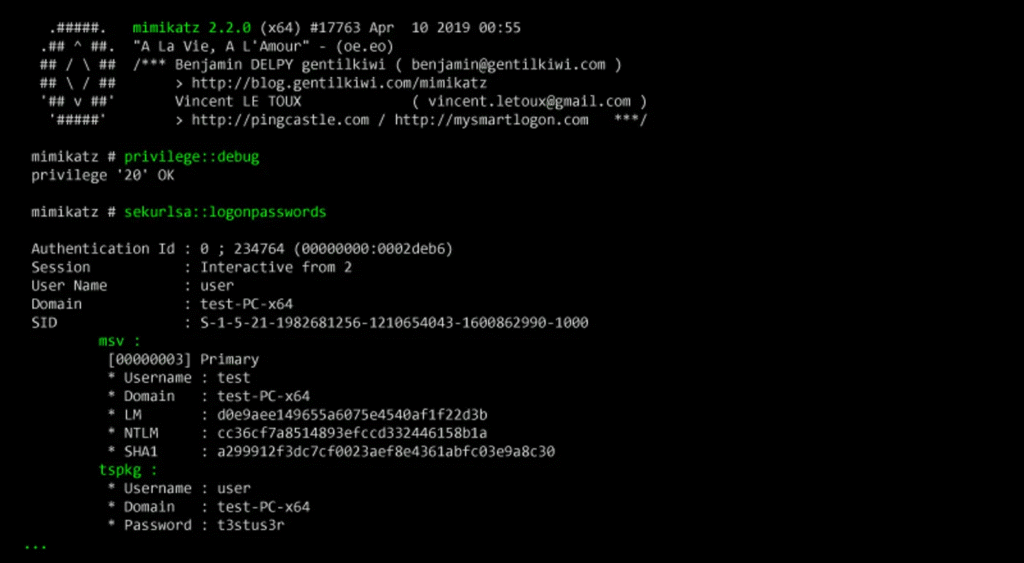
So what exactly is Mimikatz? It’s not a cartoon character or a funny app. Mimikatz is a powerful open-source tool created in 2007 by Benjamin Delpy, a French security researcher. Originally, Delpy built it to show vulnerabilities in Windows security systems—especially how Windows stored passwords in memory.
But over time, hackers grabbed onto it because it could extract passwords, PINs, and other sensitive data from a computer’s memory. Using Mimikatz, a hacker can steal login credentials and use them to move deeper into a network. It’s now one of the most widely used tools in advanced cyberattacks, especially in pass-the-hash and pass-the-ticket attacks.
Mimikatz has also become a teaching tool for ethical hackers and cybersecurity experts. They use it to test systems and find weak points before real attackers do.
What’s a Timeline Snippet in Simple Words?
Imagine a timeline like a storybook about a cyberattack. A timeline snippet is a single paragraph in that story that zooms in on a key moment—like when Mimikatz was first run on a system.
It captures specific details such as:
- The time and date Mimikatz was executed.
- The commands used by attackers.
- What credentials or data were stolen.
- How that moment fits into the bigger attack flow.
Think of it like reviewing CCTV footage but focusing on one important frame where the burglar cracks the lock. This is what cybersecurity professionals do with timeline snippets—they zoom in on crucial events to understand how hackers succeeded.
Why Do Hackers Use It?
Hackers love Mimikatz because it’s free, powerful, and easy to use. They use it to extract login credentials directly from memory without needing to crack passwords. With these credentials, attackers can impersonate users, including system admins, and gain access to sensitive systems.
A timeline snippet of this activity helps defenders figure out exactly when and how Mimikatz was deployed.
Why Is It Important in Cybersecurity?
In cybersecurity, speed and accuracy are everything. By focusing on Mimikatz-related events in a timeline, security teams can quickly see when their systems were compromised. This allows them to:
- Contain the attack faster.
- Patch vulnerabilities.
- Alert users and admins about stolen credentials.
- Prevent further damage.
Without timeline snippets, teams may spend hours or days sifting through logs trying to find the needle in the haystack.
How Does Mimikatz Work With Timeline Snippets?
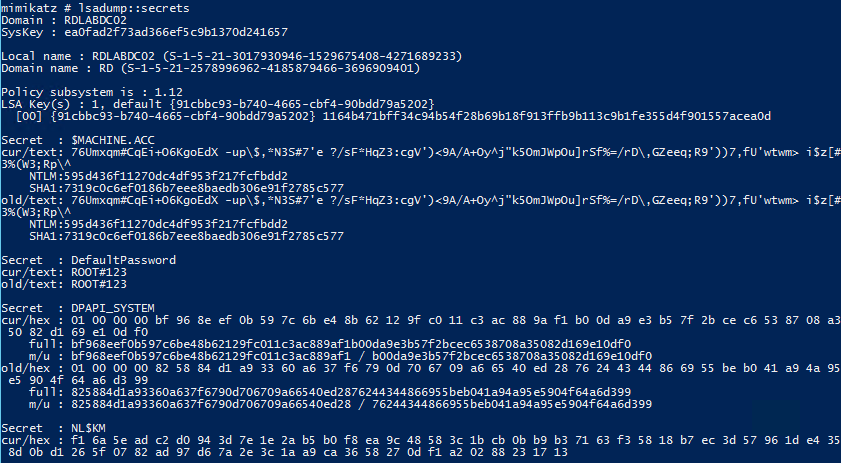
When Mimikatz runs, it leaves traces in system logs—commands executed, processes launched, and files accessed. Security tools like SIEMs (Security Information and Event Management) or EDRs (Endpoint Detection and Response) capture these traces. Analysts then extract timeline snippets focused on Mimikatz to reconstruct the attack and respond.
These snippets may show:
- When credentials were dumped.
- If attackers moved laterally to other machines.
- How long Mimikatz ran undetected.
This detailed view is critical for forensic investigations and future prevention.
Real-Life Uses of Mimikatz-Centric Timeline Snippets
In real-world cybersecurity, timeline snippets are like detective notes. They’ve helped teams uncover advanced persistent threats (APTs), ransomware campaigns, and insider attacks.
For example, after a ransomware attack, investigators might pull out a Mimikatz-centric snippet showing how attackers gained domain admin rights. This info helps them block similar attacks in the future and advise organizations on better security practices.
Banks, healthcare systems, and government agencies all use timeline snippets during post-breach investigations.
Famous Cyber Attacks Where It Appeared
Mimikatz has appeared in several high-profile attacks:
- NotPetya (2017): Hackers used Mimikatz to steal credentials and spread malware across Ukraine and beyond.
- WannaCry follow-up attacks: Attackers used Mimikatz to escalate privileges after initial infections.
- APT29 and APT38 groups: These state-sponsored groups used Mimikatz during their campaigns against US and European targets.
Each of these attacks taught cybersecurity teams more about the importance of monitoring for Mimikatz activity.
Lessons Learned From These Cases
The biggest lesson? No network is 100% safe. Even giant corporations with massive security budgets fell victim.
Here’s what security teams learned:
- Always use strong privilege management—limit admin accounts.
- Enable credential guard and secure LSASS memory.
- Monitor for abnormal processes linked to Mimikatz.
- Train staff about phishing, since it’s often the first step attackers use.
How to Stay Safe From Mimikatz Attacks
If you’re worried about Mimikatz, start by securing your Windows systems:
- Keep systems updated with the latest patches.
- Use multi-factor authentication (MFA) everywhere.
- Disable unnecessary admin privileges.
- Turn on Windows features like Credential Guard.
Also, invest in good endpoint security solutions that can detect suspicious behavior.
Tools That Detect Timeline Snippets Fast
There are powerful cybersecurity tools that help detect Mimikatz traces and create timeline snippets:
- Microsoft Defender ATP
- CrowdStrike Falcon
- Splunk
- ELK Stack (Elasticsearch, Logstash, Kibana)
- Sysmon with custom configs
These tools let teams spot Mimikatz activity and extract meaningful timeline snippets before attackers cause damage.
Key Takeaways About Mimikatz-Centric Timeline Snippets
- Mimikatz is a credential-dumping tool widely used by hackers.
- Timeline snippets help security teams focus on key moments in attacks.
- Detecting and analyzing these snippets is critical for fast response.
- Awareness and preparation are your best defenses.
About Mimikatz-Centric Timeline Snippets
In simple words, a Mimikatz-centric timeline snippet is a snapshot of when Mimikatz was active during a cyberattack. It’s not just a geeky concept—it’s a real tool helping defenders understand attacks and improve security. Whether you’re a business owner, IT admin, or just a curious reader, knowing this term can help you appreciate how cybersecurity works behind the scenes.
The Bottom Line
Cyberattacks aren’t slowing down, and tools like Mimikatz remain a favorite weapon for hackers. But with concepts like timeline snippets, cybersecurity experts are fighting back smarter. By zooming in on critical events, they can stop hackers in their tracks and protect systems before the damage spreads. Remember: understanding how these tools work—even at a basic level—can empower you to stay safer online.

